What Is a Honeypot and Can It Help Mitigate Cyberattacks?
In recent years, cyberattacks and data breaches have become increasingly common and devastating for businesses across all industries. One approach to mitigating the risk of cyberattacks is the implementation of a cybersecurity technique called a honeypot.
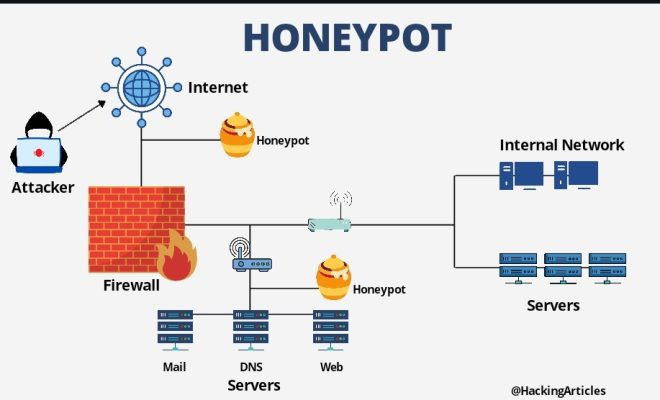
A honeypot is a cybersecurity strategy designed to attract and distract potential cyber attackers from actual networks or critical systems. It is essentially a decoy system that looks like a legitimate target, but is actually designed to lure attackers away from real networks and systems.
A honeypot can be implemented in two different ways: a low-interaction honeypot or a high-interaction honeypot. A low-interaction honeypot simulates only a few network services to deceive attackers, and the interaction is limited. High-interaction honeypots simulate a full system and allow attackers to run malware and other malicious activities, giving security teams insight into the attackers’ behavior patterns and techniques.
Honeypots can be used for a variety of reasons to help mitigate cybersecurity threats. First, they can help identify and track malicious activity. By luring attackers away from the real network, honeypots can provide information about attacker profiles, tactics, and tools. This valuable information can be used to better understand the nature of the threat, identify its source, and take appropriate mitigating actions.
Second, honeypots can help improve overall cybersecurity posture and awareness. By implementing a honeypot, organizations can better understand the vulnerabilities in their environment and improve their detection and incident response capabilities. This can also contribute to the overall security of an organization’s systems and provide an opportunity for security teams to learn and refine their security best practices.
Third, honeypots can serve as a legal deterrent against attackers. Since honeypots are designed to distract attackers from actual networks and systems, it can make it harder for attackers to cause real damage or steal valuable data. Additionally, honeypots can aid in collecting evidence against attackers, making it easier to prosecute them for their crimes.
While honeypots can provide a number of benefits to organizations looking to improve their cybersecurity, there are also some potential drawbacks to consider. One concern is that honeypots can be expensive to deploy and maintain. Additionally, honeypots may require additional resources to manage and monitor, reducing the effectiveness of the strategy.
Another potential drawback is that attackers can often detect honeypots if they have enough time and resources. This can diminish the effectiveness of the honeypot and potentially counteract its intended benefits. Additionally, attackers could potentially use honeypots to their advantage and use them to launch attacks against other systems.
In conclusion, honeypots can be an effective strategy for mitigating cyberattacks when used properly. By providing valuable data about attackers’ behavior, improving an organization’s cybersecurity posture, and serving as a legal deterrent against attackers, honeypots can be a valuable addition to any organization’s cybersecurity strategy. However, it is important to carefully consider the potential drawbacks and ensure that honeypots are properly maintained and monitored.