Cryptographic Hash Function
Cryptographic Hash Function: The Key to Secure Communications
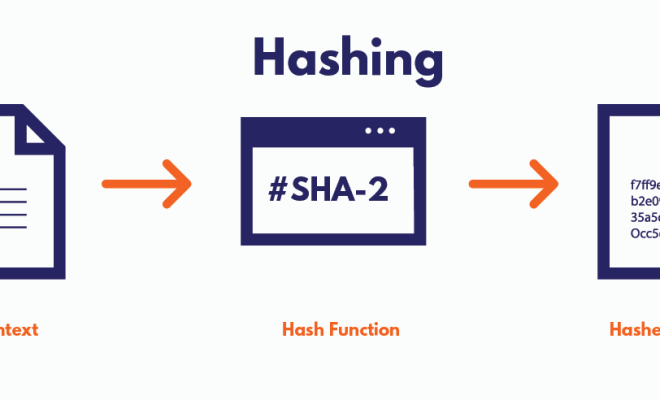
In the world of cybersecurity and cryptography, cryptographic hash functions are a crucial component to ensuring secure communications. A cryptographic hash function is a mathematical algorithm that takes in any input, no matter how large, and produces a fixed-sized output, known as a hash. The resulting hash value is unique to the input data and serves as a digital fingerprint of the original data.
There are a few key properties that make cryptographic hash functions so invaluable for secure communications. First and foremost, they are one-way functions, meaning it is infeasible to derive the original input data from the hash value. It is also highly unlikely that two different input values will produce the same hash value, known as a collision. These properties make cryptographic hash functions ideal for a variety of security applications, such as password storage, digital signatures, and verifying the integrity of data in transit.
Password Security
Password security has become increasingly important in recent years as more and more sensitive information is stored digitally. Cryptographic hash functions play a critical role in password security because they allow for the storage of passwords without actually storing the passwords themselves. Instead, the hash of the password is stored in the database, and whenever a user logs in, their password is hashed and compared to the stored hash. If the hashes match, access is granted.
This system provides an added layer of security because even if the database is breached, the attackers do not have access to the actual passwords. Instead, they would only have access to the hashed values, which are essentially useless without the correct input data. Additionally, the use of a salt, a random string of characters added to the password before hashing, helps to further protect against attacks such as precomputed hash tables and rainbow tables.
Digital Signatures
Another critical use for cryptographic hash functions is in the creation and verification of digital signatures. Digital signatures are essentially the digital equivalent of a handwritten signature, providing authentication and integrity to digital documents. To create a digital signature, a hash of the document is created using a cryptographic hash function, and the hash value is then encrypted using the signer’s private key. This creates a digital signature that can be verified using the signer’s public key.
By using a cryptographic hash function, the digital signature is tied to the specific document, ensuring that any changes to the document will result in a different hash value and therefore an invalid signature. This provides assurance that the document has not been tampered with and can be trusted. This is particularly important in industries such as finance and healthcare where the integrity of documents is critical.
Data Integrity
Finally, cryptographic hash functions are used to verify the integrity of data in transit. This is done by creating a hash of the data before it is transmitted and then sending the hash value alongside the data. The receiver of the data can then create their own hash of the data they received and compare it to the transmitted hash. If the hashes match, the data has remained unchanged during transmission, and if they do not match, the data has been tampered with.
This is a critical component of secure communications because it provides assurance that the data transferred has not been altered, either intentionally or unintentionally. This is particularly important in the world of financial transactions and online banking, where the integrity of data is paramount.
In conclusion, cryptographic hash functions are essential to secure communications in the digital age. They provide one-way functions, are highly collision-resistant, and are critical components of password storage, digital signatures, and verifying the integrity of data in transit. As the world becomes increasingly reliant on digital communications, cryptographic hash functions will continue to play a vital role in protecting our sensitive information.