A Beginner’s Guide to Metasploit in Kali Linux (With Practical Examples)
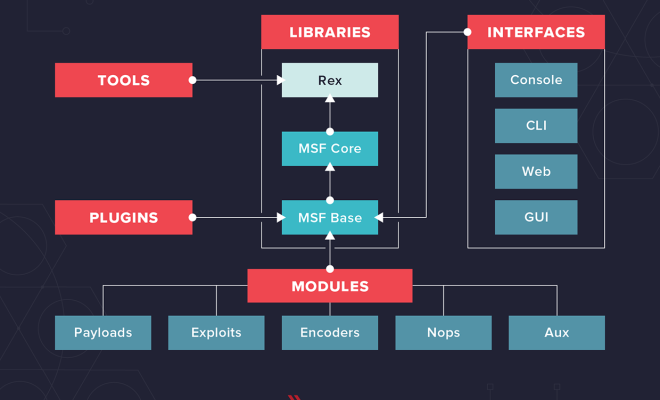
Metasploit is an open-source tool used for penetration testing and creating exploit programs. It is a powerful framework that can be used to test the security of a network or website. Metasploit is best utilized on the Kali Linux operating system. In this article, we will provide you with a beginner’s guide to Metasploit in Kali Linux with practical examples.
Step 1: Installing Metasploit
First, you need to ensure that Metasploit is installed on your Kali Linux operating system. If you have installed Kali Linux 2021.1, then it already comes pre-installed with Metasploit. If it is not installed, you can download and install it from the official Metasploit website.
Step 2: Updating Metasploit
After installing Metasploit, you need to update it regularly to keep it up-to-date with the latest exploits and vulnerabilities. You can do this by typing the following command in the terminal:
msfupdate
This command will automatically update Metasploit to its latest version.
Step 3: Running Metasploit
To start using Metasploit, open the terminal and type the following command:
msfconsole
This will start the Metasploit console, which is the interface used to interact with the Metasploit framework. You will see a banner that welcomes you to the Metasploit console.
Step 4: Finding Exploits
To start using Metasploit, you need to find exploits that you can use. The Metasploit framework has a vast database of exploits that you can use. You can search for an exploit by typing the following command:
search exploit
This command will return a list of all exploits available in the Metasploit database. You can filter the results by specifying the type of exploit you are looking for.
Step 5: Adding a Target
Once you have found an exploit, you need to add a target for the exploit to be executed. To do this, you need to create a target object by typing the following command:
use exploit/exploit_name
For example, if you want to use the MS17-010 vulnerability on Windows, you would type:
use exploit/windows/smb/ms17_010_eternalblue
Step 6: Setting the Payload
The next step is to set the payload that the exploit will use. The payload is the code that will be executed on the target system. To set the payload, you need to type the following command:
set payload payload_name
For example, if you want to use the reverse TCP payload, you would type:
set payload windows/x64/meterpreter/reverse_tcp
Step 7: Configuring the Exploit
After setting the payload, you need to configure the exploit to work properly. The configuration involves setting the target’s IP address, port number, and other parameters. You can see the available options by typing the following command:
show options
Step 8: Exploiting the Target
Once the exploit is properly configured, you can execute it by typing the following command:
exploit
This will launch the exploit and attempt to execute the payload on the target system. If successful, you will gain access to the target system and be able to perform various actions on it.
Conclusion
In this article, we have provided a beginner’s guide to Metasploit in Kali Linux with practical examples. Metasploit is a powerful tool that can be used to test the security of a network or website. With the right knowledge and understanding, Metasploit can be an effective tool in identifying and mitigating security vulnerabilities. However, it is important to remember that using Metasploit inappropriately can lead to serious legal consequences. Therefore, it is essential to have a thorough understanding of the laws and regulations governing the use of such tools.