What is Remote Desktop Protocol (RDP)?
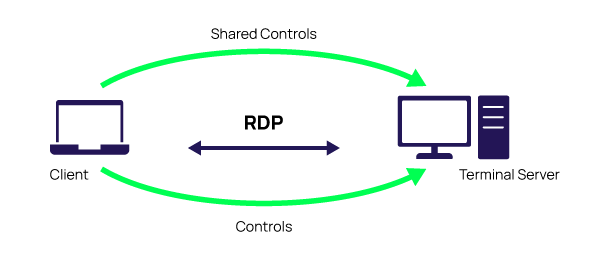
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft for remote access to Windows-based computer systems over a local area network (LAN) or the internet. It allows users to connect to a remote computer and access its desktop environment, apps, files, and resources as if they were sitting right in front of the computer. RDP is widely used by businesses, organizations, and individuals to enable remote work, remote support, and remote administration.
RDP works by transmitting user input and screen images from a remote client computer to a remote host computer and transmitting the resulting screen images back to the client. The host computer runs the remote desktop service, which manages the RDP connections and enables multiple remote sessions to be set up and managed simultaneously. The host computer can be configured to allow or deny remote connections, and to require authentication before granting access.
RDP supports a range of features and functions that make remote access more efficient and effective. These include audio and video playback, printer and file sharing, clipboard sharing, and remote control of the host computer. RDP also allows remote access to installed apps and programs, allowing users to use the remote computer as if it were their own.
One of the major advantages of RDP is its ease of use and accessibility. It is built into all Windows operating systems and can be used by anyone with a Windows computer or device. RDP also supports multiple platforms, including desktops, laptops, and mobile devices, making it a versatile solution for remote access.
However, as with any remote access solution, RDP does come with some risks and drawbacks. These include the possibility of unauthorized access or exploitation of vulnerabilities in the RDP protocol, which can result in data breaches, malware infections, or other security threats. To mitigate these risks, it is recommended that users implement proper security measures, such as using strong passwords, enabling two-factor authentication, and keeping software up-to-date.






